The Cloud Migration Imperative
As digital acceleration reshapes every industry, cloud transformation has shifted from a choice to a necessity. Organizations across sectors are moving workloads to the cloud to enhance agility, reduce costs, and unlock innovation. According to Gartner, by 2026, 75% of organizations will adopt a digital transformation model predicated on cloud as the fundamental underlying platform. Source:Gartner
From migrating legacy systems to adopting cloud-native platforms, the goal is clear: move faster, serve better, innovate continuously.
But there’s a blind spot. In the rush to modernize, many overlook a critical factor: security. It’s not enough to “lift and shift” systems or adopt cutting-edge cloud services. If security doesn’t scale with modernization, organizations risk creating new vulnerabilities faster than they can close the old ones.
“A cloud-first future is exciting – unless you forget to bring security with you.” says Dineshkumar Gandhi, Technical Project Manager at STAFIDE.
And at the heart of secure cloud transformation isn’t just technology; it’s talent.
Why Security Can’t Be an Afterthought
A common misconception in cloud adoption is that public cloud platforms are inherently secure. While cloud providers like AWS, Microsoft Azure, and Google Cloud invest heavily in their infrastructure’s security, they operate on a shared responsibility model.
Here’s what that means:
- Cloud providers secure the underlying infrastructure.
- Organizations using cloud services are responsible for securing their own data, identities, applications, and configurations.
This distinction is where many organizations fall short.
Real-World Breach
Oracle Cloud Breach Highlights Legacy Vulnerability Risks
In March 2025, Oracle Cloud suffered a major breach when a threat actor known as “rose87168” allegedly exploited a legacy vulnerability (CVE202135587) in Oracle Access Manager to access around 6 million sensitive records. The stolen data encrypted SSO and LDAP passwords, JKS files affected over 140,000 tenant environments. The attacker issued ransom threats and attempted to sell the data, exposing the dangers of unpatched legacy systems in cloud infrastructures. Security Breach of Oracle Cloud via Exploit of CVE-2021-35587
Salesforce Breach Reveals Social Engineering Weaknesses
In early 2025, cyber group UNC6040 exploited voice phishing to breach Salesforce environments by tricking employees into installing a malicious version of the Data Loader tool. Without exploiting any platform vulnerability, attackers gained access via misused cloud-native permissions, targeting many organizations across Europe and the Americas. Several victims suffered data theft and extortion, highlighting how social engineering rather than technical flaws can compromise even well-secured cloud platforms. Salesforce Ben
And they’re not alone. Misconfiguration remains one of the leading causes of cloud data breaches, especially as more organizations undergo cloud transformation.
• Accenture inadvertently exposed sensitive cloud data due to misconfigured S3 buckets during its cloud operations.
• Facebook faced public backlash when user records stored on third-party cloud servers were left exposed due to lax access controls.
Security isn’t just a checkbox. It’s a discipline that must be embedded into every stage of your cloud journey from design and deployment to ongoing operations. And that requires a skilled, proactive team.
The Role of Talent in Secure Cloud Transformation
While cloud transformation is often discussed in terms of platforms and tools, its success depends heavily on people.
Why? Because cloud environments are fluid, API-driven, and constantly evolving. Unlike traditional data centers, cloud ecosystems require adaptive thinking and continuous security vigilance.
The Hybrid Skills Gap
Modernization demands hybrid skills – professionals who:
- Understand cloud architectures and DevOps workflows
- Apply security best practices across multi-cloud environments
- Appreciate legacy systems and integration constraints
- Navigate compliance in regulated industries
These professionals act as translators and enablers, ensuring that cloud adoption doesn’t compromise the security, compliance, or continuity of business operations.
Key Roles That Anchor Secure Cloud Transformation
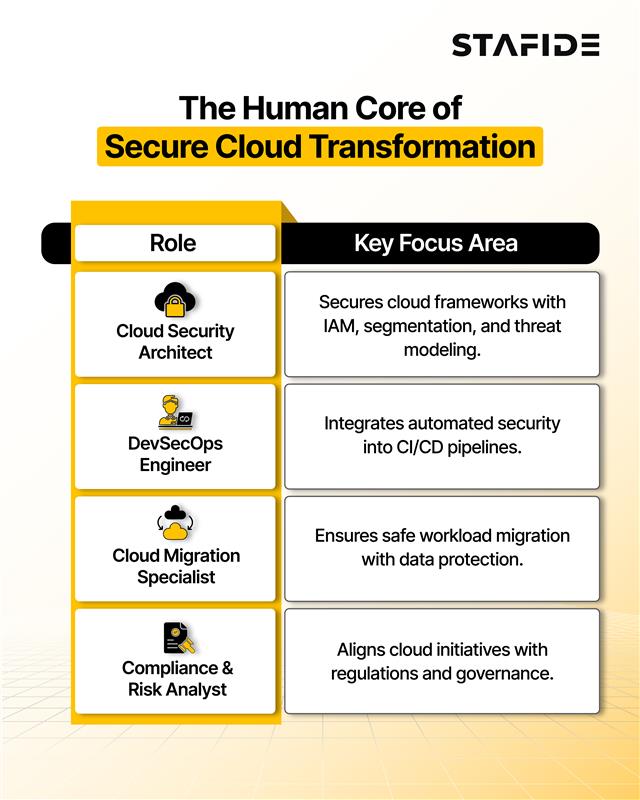
1. Cloud Security Architect
- Develops cloud-native security designs and controls
- Defines IAM policies, segmentation, and threat modeling
- Advises DevOps and infrastructure teams on security best practices
2. DevSecOps Engineer
- Embeds security into CI/CD pipelines
- Automates testing, scanning, and policy enforcement
- Builds security as code, not just as oversight
3. Cloud Migration Specialist
- Plans secure workload migrations
- Maps dependencies across legacy and cloud-native environments
- Implements data protection during transition phases
4. Compliance and Risk Analyst
- Ensures alignment with global regulatory standards (GDPR, HIPAA, CCPA)
- Conducts audits, risk assessments, and incident simulations
- Bridges IT, legal, and governance teams
Each role brings a different but critical perspective. Collectively, they enable cloud transformation that’s resilient, compliant, and future-proof.
What to Look for in Candidates
The most successful organizations don’t just hire for technical ability – they also prioritize strategic alignment.
Here’s what to look for when hiring for secure cloud transformation:
1. Proven Technical Credentials
Certifications serve as a baseline, especially when hiring for complex or regulated environments.
Look for candidates with credentials like:
- AWS Certified Security – Specialty
- Azure SC-100: Microsoft Cybersecurity Architect
- Google Cloud Professional Security Engineer
- (ISC)² Certified Cloud Security Professional (CCSP)
- Certified Kubernetes Security Specialist (CKS)
These certifications ensure a foundational understanding of security principles and cloud-native architecture.
2. Experience with Security Operations in Cloud Environments
Beyond certifications, practical experience matters:
- Designing and securing VPCs, subnets, and IAM roles
- Implementing encryption and key management systems
- Using tools like CloudTrail, Azure Security Center, or GCP’s Security Command Center
- Integrating SIEMs and security tools into DevOps workflows
- Building incident response playbooks tailored for cloud platforms
Look for familiarity with frameworks like:
- NIST 800-53
- CIS Controls
- ISO/IEC 27001
3. Soft Skills and Leadership Qualities
Cybersecurity is a team sport. Candidates should be:
- Excellent communicators – to bridge technical and non-technical stakeholders
- Strategic thinkers – who align security efforts with business objectives
- Collaborators – especially in fast-moving Agile or DevSecOps environments
Strong hires also demonstrate curiosity and a willingness to evolve with the threat landscape.
“Technology changes fast. Security changes faster. The best cloud security talent never stops learning.” as highlighted by Gokulakrishnan Nagarajan, HR Lead at STAFIDE.
Hiring Strategies That Work

How can organizations attract and retain the right talent with specialized cloud expertise in cybersecurity?
1. Look Beyond Job Boards:
General job platforms often miss niche candidates. Instead:
- Use cybersecurity-specific job boards (e.g., ClearedJobs, CyberSecJobs)
- Attend cloud security conferences (e.g., AWS re:Inforce, RSA Cloud Security Track)
2. Assess for Skills, Not Just Resumes
Create real-world challenges to evaluate how candidates:
- Harden an exposed S3 bucket
- Fix broken IAM permissions
- Deploy and monitor a secure container workload
Platforms like Hack The Box, Cloud Academy, or Immersive Labs can simulate practical environments.
3. Invest in Internal Upskilling
Sometimes, the best candidate already works for you. Train existing IT, DevOps, or software engineers with:
- Cloud-specific security bootcamps
- Sponsored certifications (CCSP, CKS)
- Job rotations between security and cloud engineering teams
According to LinkedIn’s 2024 Workplace Learning Report, 94% of employees would stay longer at companies that invest in their career development. LinkedIn Learning
4. Embrace Diverse Backgrounds
Don’t restrict your talent pool. Look beyond degrees:
- Veterans with intelligence or defense experience
- Developers who transitioned into security
- Professionals with open-source contributions or self-paced learning
This expands your hiring options and brings fresh, unconventional thinking.
5. Prioritize Mission and Culture Fit
Top cloud security professionals want purpose. Position your company as:
- Committed to secure digital transformation
- Willing to give security a “seat at the table”
- Focused on ethical, transparent, and resilient systems
Involve them early in projects, not as afterthoughts.
“Security isn’t a checkbox; it’s a culture. And culture starts with who you hire.”
6. Finding a Compatible Hiring Partner
Building secure cloud teams demands expertise, not just headcount. The right hiring partner aligns talent strategy with your modernization goals, delivering both speed and precision.
The right partner will:
- Understand your organization’s cloud maturity and security roadmap
- Identify and attract pre-vetted, certified professionals (e.g., CCSP, AWS Security Specialty, Azure SC-100)
- Offer flexible models from contract-based specialists to permanent hires to match project needs
Ensure cultural alignment and retention by focusing on long-term team fit
Secure Modernization Starts with People
As organizations modernize their IT infrastructure, security should never be sacrificed for speed. Cloud transformation delivers true agility only when it’s built on a foundation of trust, talent, and thoughtful strategy.
While cloud platforms offer incredible capabilities, they don’t protect themselves. Tools like IAM, threat detection, encryption, and compliance monitoring are powerful, but they’re only as effective as the people configuring and managing them.
By embedding security expertise early in your transformation, you can:
- Reduce risk exposure
- Build resilient architectures
- Accelerate innovation with confidence
In other words: modernization without compromise is not only possible; it’s essential. And it starts with the people you hire.
Build Secure, Cloud-Ready Teams with STAFIDE
Looking to build a secure, cloud-ready workforce that drives real transformation?
Partner with STAFIDE who understands the intersection of recruitment, cybersecurity, and enterprise modernization. Whether you’re building a cloud-native team from scratch or upskilling your internal talent, now is the time to act.
Security starts with strategy. Strategy starts with talent
h talent