With cyberattacks becoming more frequent, complex, and costly, the Security Operations Center (SOC) is now the frontline of enterprise defense. But many SOCs are weighed down by legacy systems, fragmented tools, and manual workflows.
The result? Delayed response times, alert fatigue, and growing burnout, especially in understaffed teams. According to IBM’s 2025 Cost of a Data Breach Report, the average global cost of a data breach is now $4.4 million per incident, reflecting improvements in detection and containment driven in large part by AI-powered defenses.
As cloud adoption and hybrid work expand the attack surface, traditional SOC models fall short. To keep pace, organizations must invest in modern platforms, streamlined processes, and empowered people ready to lead the next generation of cyber defense.
The New Reality: Complexity, Scale, and Speed
The current cybersecurity environment is shaped by three defining pressures: complexity, scale, and speed. The rapid shift to hybrid work, widespread cloud adoption, and the proliferation of connected devices have dramatically expanded the attack surface. At the same time, adversaries are leveraging sophisticated techniques including automation, AI-driven phishing, and supply chain exploits to evade traditional defenses, adding new layers of complexity.
Security Operations Centers (SOCs) built on legacy infrastructure and reactive processes are struggling to keep pace. The sheer scale of daily security events, combined with the high rate of false positives, overwhelms many SOC teams, draining resources and delaying response times. As threats emerge and evolve faster than ever, speed becomes a critical differentiator yet too often, SOCs are slowed down by manual workflows and alert fatigue.
To stay ahead, organizations must embrace a modern SOC model—one that integrates intelligent automation, streamlines alert management, and enables real-time detection and response. Complexity, scale, and speed are no longer just challenges they are the operating conditions of cybersecurity today.
What a SOC Does ?
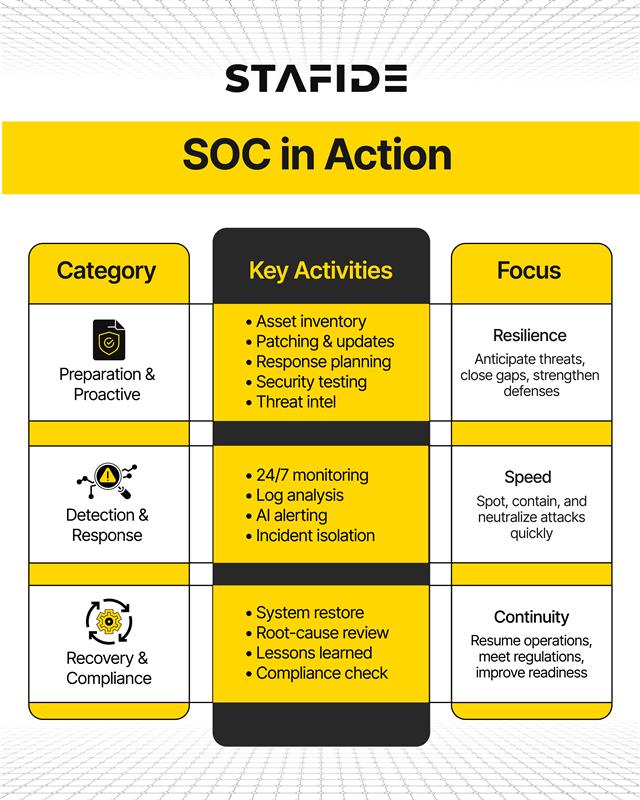
A Security Operations Center (SOC) plays a pivotal role in safeguarding an organization’s cybersecurity. SOC activities and responsibilities generally fall into three primary categories:
Preparation and Proactive Measures
- Asset Inventory: Maintain an up-to-date inventory of all assets (applications, servers, endpoints, etc.) and security tools using asset discovery tools.
- Routine Maintenance: Regular software patches, firewall updates, and continuous refinement of security policies are crucial for effectiveness.
- Incident Response Planning: Develop a clear plan with defined roles, responsibilities, and metrics for handling security events.
- Regular Testing: Conduct vulnerability assessments and penetration tests to identify and fix system weaknesses.
- Staying Current: Stay informed on emerging technologies, tools, and threat intelligence from diverse sources.
Real-Time Threat Detection and Response
- Continuous Monitoring: Monitor the IT infrastructure 24/7 for potential threats.
- Log Management: Analyze log data to detect anomalies and establish baselines of normal activity.
- Threat Detection: Sort alerts by severity and use AI to automate detection and improve response.
- Incident Response: Investigate and isolate threats quickly by disconnecting compromised endpoints and blocking malicious traffic.
Recovery and Compliance
- Recovery and Remediation: Restore systems to pre-incident state, including restoring backups and resetting passwords.
- Post-Mortem and Refinement: Analyze incidents to improve security policies, tools, and response strategies.
- Compliance Management: Ensure adherence to security regulations (GDPR, HIPAA, PCI DSS) and collaborate with legal teams for notifications.
Why Your Organization Needs a SOC ?
The establishment of a SOC offers a range of significant benefits for an organization:
Asset Protection: A SOC helps prevent unauthorized access and minimizes the risk of data breaches, safeguarding critical systems, sensitive data, and intellectual property.
Business Continuity: By preventing and minimizing the impact of security incidents, SOCs ensure that business operations remain uninterrupted, maintaining productivity and customer satisfaction.
Regulatory Compliance: SOCs facilitate compliance with cybersecurity regulations by implementing effective security measures and maintaining records of incidents and responses.
Cost Savings: Proactive security measures provided by SOCs can save organizations significant costs by preventing expensive data breaches and cyberattacks, reducing the need for in-house security personnel in some cases.
Customer Trust: The operation of a SOC signals a commitment to cybersecurity, enhancing trust among customers and stakeholders.
Enhanced Incident Response: SOCs’ rapid response capabilities limit downtime, reduce financial losses, and restore normal operations quickly.
Improved Risk Management: By analyzing security trends and events, SOC teams can proactively identify vulnerabilities and take preventive measures to reduce risk.
Proactive Threat Detection: Continuous monitoring and automated threat detection allow SOCs to quickly identify and mitigate risks, helping organizations stay ahead of an evolving threat landscape.
The Key Roles Fueling Your SOC’s Success
A successful SOC team is made up of various experts, each responsible for different aspects of cybersecurity operations:
SOC Manager: The SOC Manager leads the team and oversees all security operations. They report directly to the Chief Information Security Officer (CISO) and ensure the team is aligned with organizational security goals.
Security Engineers: These professionals are responsible for building, managing, and maintaining the organization’s security infrastructure. Their work involves evaluating, testing, and deploying security tools and technologies and collaborating with development teams to ensure security measures are integrated into application development.
Security Analysts: Often referred to as security investigators or incident responders, analysts are the first line of defense when a cybersecurity threat or incident occurs. They detect, investigate, triage, and respond to potential security incidents. Depending on the organization, this role may be split into Tier 1 (investigators) and Tier 2 (incident responders) roles.
Threat Hunters: These experts specialize in proactively searching for advanced threats that might bypass automated security defenses. They conduct deep dives to identify emerging or unknown threats and contain them before they cause significant damage.
Other Specialists: Depending on the size and nature of the organization, the SOC team may include roles like the Director of Incident Response, who coordinates and communicates during a security incident, and forensic investigators, who retrieve crucial data from compromised systems for analysis. Larger organizations may have additional specialists depending on their cybersecurity needs.
Empowering People for Stronger Security Operations
An effective Security Operations Center (SOC) starts with empowered analysts. Reducing alert fatigue and providing contextual data doesn’t just help teams detect threats faster, it also fosters a culture of resilience. This understanding is gaining traction within the cybersecurity community, where the human element is recognized as being just as crucial as technology.
Burnout has become one of the top operational challenges for SOC teams, driven largely by overwhelming alert volumes and reactive workflows. A shift in mindset is necessary to address this issue. Leading organizations are rethinking how SOC teams operate by implementing platforms that filter noise, prioritize high-fidelity alerts, and offer meaningful context. The result is stronger team engagement, faster incident resolution, and a workforce that is both more effective and energized.
Empowering SOC teams means giving analysts the autonomy, trust, and tools they need to thrive. When the people behind security are supported, the entire security posture improves.
The Human Impact: A More Empowered Workforce
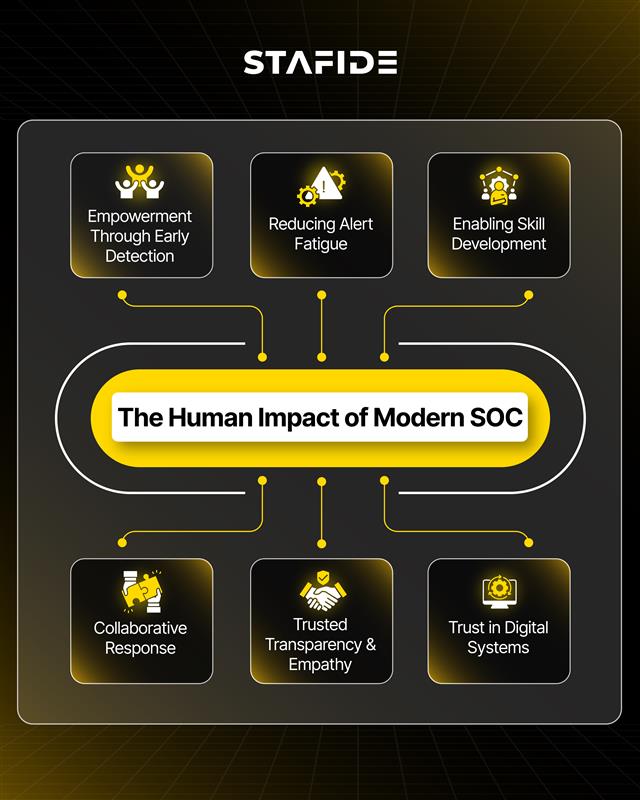
Technology alone won’t save us. A human-centric SOC doesn’t just protect infrastructure; it empowers people across the organization to do their best work, without fear of compromise. The impact is both profound and far-reaching:
- Empowerment Through Early Detection: By reducing the chance of a successful attack, SOCs protect employee data, ensure operational continuity, and safeguard digital experiences for users and customers alike.
- Reducing Alert Fatigue: SOCs powered by automation and contextual AI allow analysts to focus on meaningful work, reducing burnout and fostering job satisfaction in what is otherwise a high-pressure environment.
- Enabling Skill Development: As SOCs integrate advanced tools like XDR and AI threat modeling, analysts gain exposure to the latest in cybersecurity tech, turning everyday tasks into valuable learning opportunities that accelerate career growth.
- Collaborative Response: Effective SOCs break down silos between security, IT, risk, and compliance teams. This cross-functional collaboration not only speeds incident response but also cultivates a sense of shared responsibility and purpose.
- Transparency & Empathy: SOCs that prioritize communication and context ensure that stakeholders understand the what and why of incident response decisions, creating a culture of trust rather than fear.
- Trust in Digital Systems: When employees and customers know that their data is protected by a capable SOC, they feel confident engaging with digital services, ultimately increasing technology adoption and productivity.
–In essence, “A well-architected SOC is not just a technical asset—it’s a cornerstone of organizational well-being and innovation.”
Looking Ahead: The Future of the SOC

As cyber threats grow more sophisticated and relentless, the Security Operations Center must evolve beyond its traditional boundaries. We are entering the age of AI-augmented, cloud-native SOCs – where intelligence, agility, and business alignment are no longer aspirational, but essential.
Intelligent Automation and AI: Advanced technologies like artificial intelligence and machine learning are transforming SOC operations. By automating repetitive tasks, surfacing predictive insights, and reducing false positives, AI is helping analysts focus on what truly matters – strategic, high-impact decision-making.
Behavior-Driven Detection: Modern SOCs are leaning into behavioral analytics to identify subtle anomalies in user and system activity. Instead of relying solely on static rule sets, these systems learn and adapt, catching threats that would otherwise evade traditional detection methods.
Born for the Cloud: The architectural foundation of the SOC is changing. Cloud-native and hybrid SOCs are designed for speed, scalability, and resilience critical for organizations embracing distributed environments and multi-cloud strategies.
Zero Trust Built In: Zero Trust principles, continuous authentication and verification for all users and devices are now core to SOC design. This paradigm shift strengthens defenses in an increasingly borderless digital landscape.
From Reactive to Proactive: Proactive threat hunting is becoming a defining capability. Instead of waiting for alerts to trigger action, modern SOC teams are actively seeking out indicators of compromise to stay ahead of adversaries.
Market Momentum and Accessibility: SOC-as-a-Service (SOCaaS) is making enterprise-level cybersecurity available to small and mid-sized businesses. Investor confidence is fueling innovation, especially in AI-powered SOC tools that are transforming threat detection and response.
A Business-Critical Force: The SOC of tomorrow is more than a security function, it’s a business enabler. It safeguards digital trust, supports innovation, and empowers people. As threats evolve, so must our defenses and it starts with a future-ready, human-first Security Operations Center.
Power Your SOC with the Right People
A next-generation SOC needs more than tools. It also needs skilled talent to make them work. Stafide connects you with cybersecurity professionals who can modernize, scale, or build your SOC from the ground up.
Partner with us to create a people-powered SOC ready for today’s fast-paced threat landscape.





