Cybersecurity Talent in High Demand
The global cybersecurity job market is booming, with an estimated 3.5 million positions currently unfilled – an unmistakable signal of the critical demand for skilled professionals.
Source: AI Impact On Cybersecurity Jobs in 2025
The growing frequency and complexity of cyber threats are driving organizations to prioritize cybersecurity as a central part of their risk management strategies. Cybersecurity professionals now play a crucial role in protecting sensitive data, infrastructure, and customer trust across all sectors. As digital transformation reshapes business operations, cybersecurity has evolved from a technical field to a strategic enabler. Today, cybersecurity talent is needed not only for real-time defense but also to guide long-term security policies. This article outlines the top cybersecurity career paths for 2025, highlighting the essential skills and responsibilities.
Finding Your Fit in Cybersecurity
Choosing a cybersecurity career path begins with assessing your strengths and interests — whether you prefer hands-on technical work or strategic oversight. Consider your technical skills and leadership potential to determine if roles like security engineering or cybersecurity management are a better fit. Your background, such as experience in coding, risk analysis, or project management, can guide you toward specialized roles. For those with business or leadership experience, governance, risk, and compliance (GRC) positions are rewarding, as they leverage organizational insight and stakeholder management to drive security initiatives.
Transitioning into Cybersecurity
Cybersecurity offers entry points for established professionals, especially those with advanced degrees or leadership experience. These individuals can often transition directly into mid- or senior-level roles by leveraging transferable skills. Business leaders, with their expertise in organizational risk, strategic planning, and resource management, can smoothly move into cybersecurity by building foundational technical knowledge that aligns with their career goals.
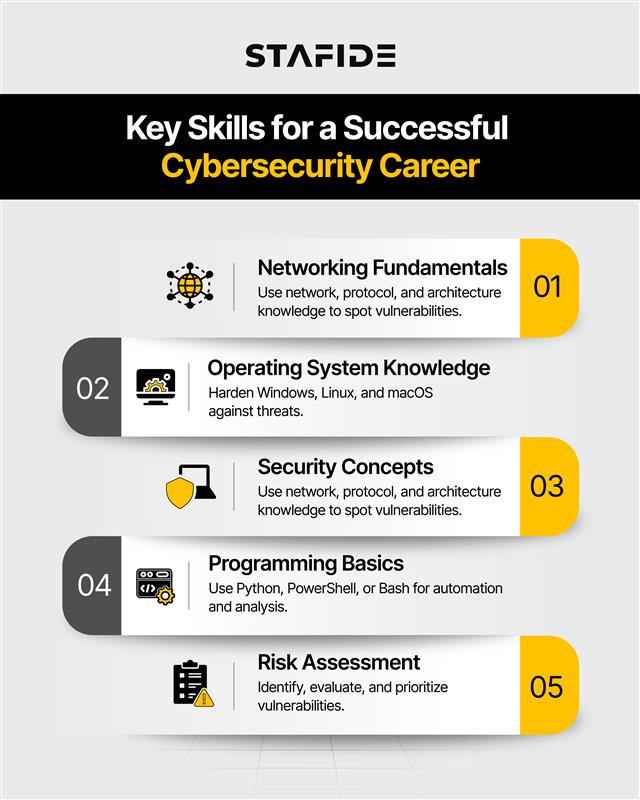
Essential Technical Skills for Cybersecurity Transitions:
- Networking Fundamentals: Understanding how computer networks operate, including protocols, architecture, and common vulnerabilities.
- Operating System Knowledge: Proficiency in Windows, Linux, and macOS, focusing on security features and weaknesses.
- Security Concepts: Familiarity with defense-in-depth, least privilege, encryption, and typical attack vectors.
- Programming Basics: Ability to interpret code in languages like Python, PowerShell, or bash for threat analysis and task automation.
- Risk Assessment: Competence in identifying vulnerabilities and prioritizing remediation based on risk and impact.
Cybersecurity Specialization vs. Generalization
When planning your cybersecurity career, you must decide whether to specialize or take a more generalized approach. Specialists build deep expertise in areas like cloud security or penetration testing, making them experts in high-demand fields. On the other hand, generalists gain a broad understanding of cybersecurity, positioning themselves for leadership roles that require cross-functional insight and strategic oversight. Specializing suits those who enjoy technical intricacies, while a generalist path offers versatility for managing teams and shaping broader security policies.
IT Professionals Making the Cybersecurity Leap
Professionals from adjacent fields, particularly IT, are well-positioned to transition into cybersecurity roles by building on their existing expertise. With a solid foundation in systems, networks, or development, many find that the shift into cybersecurity is both natural and rewarding.
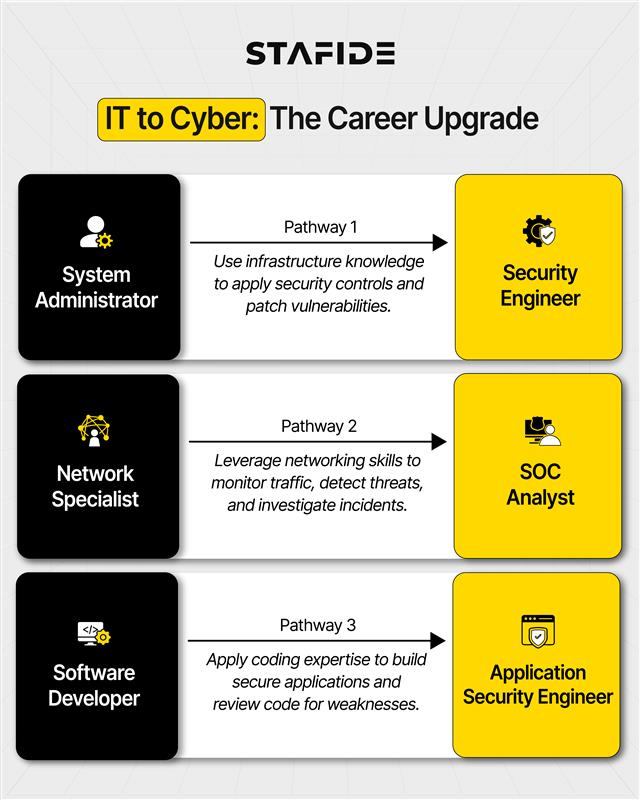
Here are some common career transition pathways for IT professionals seeking to apply their existing skills to cybersecurity roles:
- System Administrators → Security Engineers: Use infrastructure expertise to implement security controls and identify system vulnerabilities.
- Network Specialists → SOC Analysts: Apply networking knowledge to monitor traffic, detect anomalies, and investigate incidents.
- Software Developers → Application Security Engineers: Leverage coding skills to embed security in the development lifecycle and review code for vulnerabilities.
While these transitions build on existing strengths, professionals typically benefit from supplementing their knowledge with cybersecurity-specific certifications such as CompTIA Security+, CISSP, or targeted training programs to validate their understanding of security principles and prepare for more specialized responsibilities.
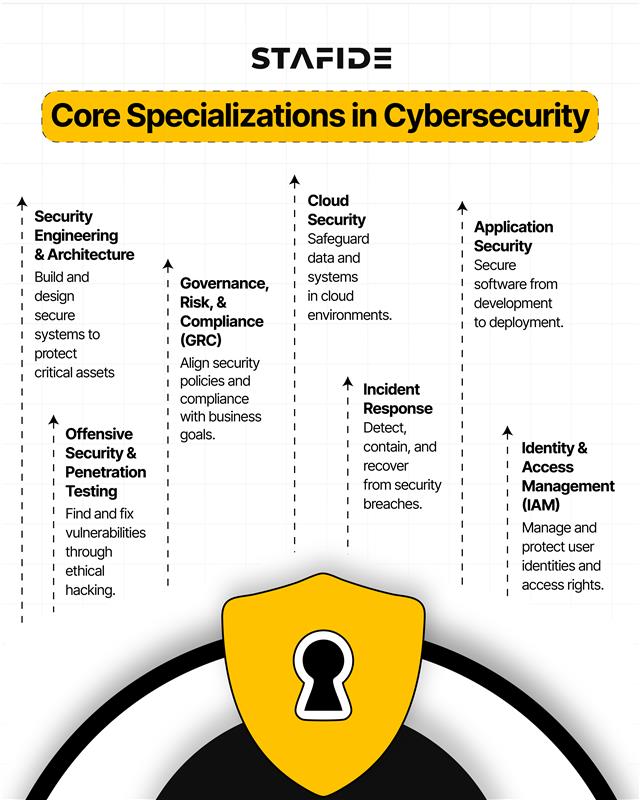
Cybersecurity Career Paths for 2025
Cybersecurity offers a wide range of roles to match different skill sets, interests, and career goals. Below are eight of the most in-demand and impactful career paths for 2025 – each with its own focus, responsibilities, and growth potential
Security Engineering and Architecture
Security engineers are responsible for building and maintaining the systems that serve as the foundation of an organization’s security. As cybersecurity careers advance, these roles typically evolve from implementing security measures to designing comprehensive security frameworks.
Specializations in Security Engineering
- Security Engineer: Implements and manages security solutions such as firewalls, intrusion detection systems, and endpoint protection to enhance an organization’s security posture.
- Security Architect: Designs comprehensive security frameworks that align with business objectives, safeguarding critical assets from unauthorized access and cyber threats.
- Cloud Security Engineer: Specializes in securing cloud-based infrastructure and applications, applying security controls tailored to major cloud platforms.
- Network Security Specialist: Focuses on securing communication channels, implementing network segmentation, and monitoring for suspicious traffic patterns.
Responsibilities in Security Engineering and Architecture
- Tool Configuration: Install and manage security technologies, including firewalls, intrusion detection systems, and endpoint protection solutions.
- Monitoring Activities: Analyze system logs and security alerts to identify potential threats and unauthorized access attempts.
- Patch Management: Apply security updates across systems to fix vulnerabilities and ensure a strong security posture.
- Security Testing: Perform regular assessments to detect system weaknesses and prevent exploitation by cyber attackers.
Documentation: Develop and update comprehensive security procedures, configurations, and system architecture diagrams.
Offensive Security and Penetration Testing
Offensive security professionals, or ethical hackers, identify vulnerabilities by simulating real-world cyberattacks. They test defenses and enhance security measures using controlled, adversarial techniques before malicious actors can exploit them.
Key Roles in Offensive Security
- Tester: Performs authorized simulated attacks on systems, networks, and applications to identify vulnerabilities before they can be exploited by malicious actors.
- Red Team Operator: Collaborates as part of a team that simulates sophisticated cyberattacks to Penetration assess an organization’s detection and response capabilities through extended campaigns.
- Vulnerability Researcher: Identifies and analyzes new security flaws in software, hardware, or protocols, often creating proof-of-concept exploits to demonstrate their potential impact.
Technical Requirements for Offensive Security Practitioners
- Networking Fundamentals: A strong understanding of protocols, routing, and network infrastructure to effectively test network-based security controls.
- Operating System Internals: Knowledge of Windows, Linux, and macOS systems to identify and exploit security vulnerabilities and misconfigurations.
- Web Technologies: Familiarity with modern web frameworks, APIs, and common vulnerabilities that impact web applications.
- Programming Skills: Ability to write custom scripts and modify existing exploits using languages like Python, PowerShell, and Bash.
- Security Tools: Proficiency with both automated scanning platforms and manual exploitation frameworks used in penetration testing.
Incident Response
Incident response professionals are frontline defenders during security breaches. They identify, contain, eradicate, and recover from incidents, minimizing organizational damage.
Specialized Roles in Incident Response
- Incident Responder: Manages the immediate response to security incidents, containing threats, restoring normal operations, and preserving evidence according to established procedures.
- Digital Forensic Analyst: Examines compromised systems to identify attack vectors, affected assets, and attacker actions by analyzing digital evidence with specialized tools and techniques.
- Threat Hunter: Actively seeks out malware and indicators of compromise that have bypassed automated detection systems within the organization’s network.
Required Skills for Incident Response Professionals
- Malware Analysis: Knowledge of how different types of malicious software function, spread, and hide within systems.
- Network Forensics: Ability to analyze network traffic, spot anomalies, and trace attack paths through complex infrastructures.
- Log Investigation: Expertise in collecting, correlating, and interpreting logs from various sources to reconstruct security incidents.
- Memory Forensics: Skill in capturing and analyzing system memory to detect malicious code and unauthorized activities.
- Communication Under Pressure: Ability to document findings clearly and coordinate response efforts with stakeholders during high-pressure situations.
Governance, Risk, and Compliance (GRC)
The governance, risk, and compliance (GRC) path focuses on the business side of cybersecurity. GRC professionals translate technical security concepts into business terms and ensure organizational practices meet regulatory requirements and industry standards.
Focus Areas for GRC Specialists
- Policy Development: Creating security policies, standards, and procedures to define organizational expectations.
- Risk Assessment: Identifying threats, evaluating vulnerabilities, and assessing potential business impacts to inform security investments.
- Compliance Management: Ensuring adherence to industry regulations, government requirements, and international standards.
- Security Metrics: Developing metrics to monitor security program effectiveness and demonstrate value to stakeholders.
- Third-Party Risk: Assessing and monitoring the security practices of vendors, partners, and service providers with access to company resources.
Required Skills for GRC Professionals
- Communication Excellence: Ability to explain complex security concepts to non-technical audiences, including executives and staff.
- Business Alignment: Balancing security needs with business objectives, finding solutions that protect assets without hindering operations.
- Regulatory Knowledge: Strong understanding of compliance frameworks, standards, and legal requirements.
- Project Coordination: Experience managing cross-functional projects with diverse stakeholders and priorities.
- Documentation Expertise: Skilled in creating clear, comprehensive documentation for internal guidance and external audits.
Cloud Security
As organizations move critical assets to the cloud, security professionals must adjust their strategies to protect data and applications in these evolving environments. Cloud security has become one of the fastest-growing IT specializations, blending traditional security practices with new cloud-specific challenges.
Responsibilities of Cloud Security Specialists
- Identity and Access Management: Implementing proper authentication and authorization controls for cloud resources.
- Data Protection: Securing sensitive information through encryption, tokenization, and access controls across cloud environments.
- Compliance Maintenance: Ensuring cloud deployments meet regulatory and industry standards despite distributed architecture.
- Security Monitoring: Monitoring cloud services for suspicious activities and potential breaches.
Required Knowledge for Cloud Security Professionals
- Cloud Platforms: Proficiency with major providers (AWS, Azure, Google Cloud) and their native security tools and architectures.
- Infrastructure Automation: Knowledge of infrastructure-as-code tools like Terraform, CloudFormation, and ARM templates for defining cloud resources.
- Containerization: Familiarity with Docker, Kubernetes, and container security practices for securing dynamic workloads.
- Serverless Security: Understanding of function-as-a-service security and protection of event-driven architectures.
- Network Security: Applying traditional network security concepts to cloud environments, including virtual networks and software-defined perimeters.
Application Security
Application security specialists focus on integrating security into applications from the start, rather than adding it later. This discipline connects security teams and developers through collaborative processes and tools to address vulnerabilities early in development.
Responsibilities of Application Security Professionals
- Secure Coding Practices: Establishing guidelines to help developers avoid common vulnerabilities from the outset.
- Security Testing: Implementing static analysis, dynamic scanning, and manual code reviews throughout the development process.
- DevSecOps Integration: Embedding security controls within automated CI/CD pipelines to ensure consistent protection.
- Third-Party Component Management: Evaluating external libraries and dependencies for security risks.
Essential Skills for Application Security Professionals
- Vulnerability Assessment: Understanding common security flaws, such as injection attacks, broken authentication, and insecure configurations.
- Secure Coding Principles: Knowledge of defensive programming techniques and language-specific security best practices.
- Testing Methodologies: Experience with static analysis, dynamic scanning, and penetration testing techniques.
- Software Development: Programming skills to review code, understand architecture, and communicate effectively with developers.
- Risk Assessment: Ability to prioritize vulnerabilities based on their potential impact and likelihood of exploitation in specific business contexts.
Identity and Access Management (IAM)
As traditional network boundaries fade, identity has become the new security perimeter. IAM specialists ensure that the right individuals access the right resources for the right reasons, protecting against unauthorized access.
Core Focus Areas of IAM Professionals
- Authentication Systems: Implementing multi-factor authentication, single sign-on, and passwordless technologies.
- Access Governance: Establishing processes for access requests, approvals, reviews, and certification.
- Identity Lifecycle Management: Automating user provisioning and de-provisioning across systems.
- Privileged Access Management: Securing and monitoring high-value administrator accounts.
Technical Requirements for IAM Specialists
- Directory Services: Proficiency with Active Directory, LDAP, and cloud identity providers that support identity infrastructures.
- Federation Protocols: Understanding SAML, OAuth, and OIDC standards for secure authentication across systems.
- Identity Governance: Knowledge of frameworks and tools for managing access rights, entitlements, and certifications.
- Cloud Identity Solutions: Experience managing identities in cloud platforms and SaaS applications.
- Security Architecture: Ability to design identity controls that balance robust security with a seamless user experience in complex environments.
Your Cybersecurity Career, Powered by Possibility
Cybersecurity is not just a job anymore – it is a mission. Whether you are diving into threat hunting, cloud security, or governance and compliance, there is never been a better time to make your move. The field is evolving fast, and so are the opportunities.
At Stafide, we shape careers and build future-proof teams. Our talent acquisition, consulting, and workforce transformation strategies are all about connecting professionals with roles that truly advance their careers, while helping businesses stay ahead of cyber threats with the right skills in place.
For job seekers, this means taking that next big step forward. For employers, it’s about finding agile, aligned cybersecurity talent ready to make an impact.
Let’s build the future – together.
Ready to explore where your cybersecurity career can go? Or need top-tier talent to strengthen your team? Get in touch with Stafide today.