Staying Ahead of Cyber Threats with CTEM
As cyber threats grow increasingly sophisticated and attack surfaces expand across hybrid infrastructures, organizations can no longer afford to be reactive in their approach to cybersecurity. Traditional methods of addressing threats only after detection are no longer sufficient in the face of modern challenges. Cyber adversaries are now more agile, utilizing advanced techniques that exploit vulnerabilities in real-time, often before organizations can even respond. This is where Continuous Threat Exposure Management (CTEM) steps in. Unlike static security measures, CTEM offers a proactive, dynamic approach that helps reduce attack surfaces and enhances an organization’s ability to detect and respond to threats before they can be exploited. By applying real-time monitoring and adaptive defenses, CTEM enables organizations to stay ahead of attackers, minimizing vulnerabilities and limiting the potential for breaches.
How People Drive CTEM Success?
The success of CTEM goes beyond technology—it requires skilled professionals to operationalize and manage its processes. While tools like threat intelligence platforms, vulnerability management systems, and automated remediation play a vital role, their effectiveness is directly tied to the talent running them. The complexity of CTEM demands a multidisciplinary team to manage the iterative stages of identifying, assessing, and remediating threats. Despite its growing importance, many organizations face challenges in filling these specialized roles, leaving critical gaps in areas where talent is most needed. As CTEM shifts cybersecurity from a reactive to a proactive defense strategy, its true potential can only be realized when the right people are in place to drive its implementation, ensuring the framework evolves into an effective, operationalized defense mechanism rather than a theoretical strategy.
What is CTEM ?
Continuous Threat Exposure Management (CTEM) is a proactive and continuous cybersecurity approach that identifies, prioritizes, validates, and mitigates threats by regularly assessing an organization’s attack surface, testing defenses, and addressing vulnerabilities in real time to reduce overall risk.
Unlike traditional vulnerability management, which often operates in silos, CTEM provides a holistic view of an organization’s security posture. It emphasizes continuous monitoring, real-time risk assessment, and adaptive response strategies to emerging threats.
Gartner predicts that organizations adopting CTEM programs will reduce security breaches by two-thirds by 2026. Gartner Identifies the Top Cybersecurity Trends for 2024
This statistic underscores the transformative power of CTEM
Building a Proactive Cyber Defense
Continuous Threat Exposure Management (CTEM) combines foundational cybersecurity practices with real-time, proactive defense mechanisms to keep organizations ahead of evolving threats. Key components include asset discovery to ensure full visibility, threat intelligence to outpace attackers, and continuous vulnerability management to minimize risks. Through attack path analysis and risk assessments, organizations can prioritize high-impact threats and fine-tune defenses. Security testing, automated remediation, and continuous monitoring create a feedback loop that strengthens defenses and accelerates response. Together, these components form a dynamic approach to cybersecurity resilience that adapts in real time, ensuring that risks are always managed before they turn into major threats.
Navigating the Challenges of CTEM Adoption
Transitioning to a Continuous Threat Exposure Management (CTEM) program can be challenging, especially when security teams operate in silos—such as vulnerability management, threat intelligence, and incident response. These silos hinder collaboration and miss valuable opportunities for integrated defense. Additionally, skill gaps in managing CTEM platforms often lead to resistance to change, slowing adoption. To overcome these hurdles, organizations must foster a culture of collaboration, break down silos, and invest in automation to streamline processes. Offering training and certification programs to upskill teams is essential, while a phased rollout combined with clear communication of CTEM’s benefits—like improved security and reduced risks—ensures a smoother transition and long-term success.
A Dynamic Framework for Proactive Cybersecurity
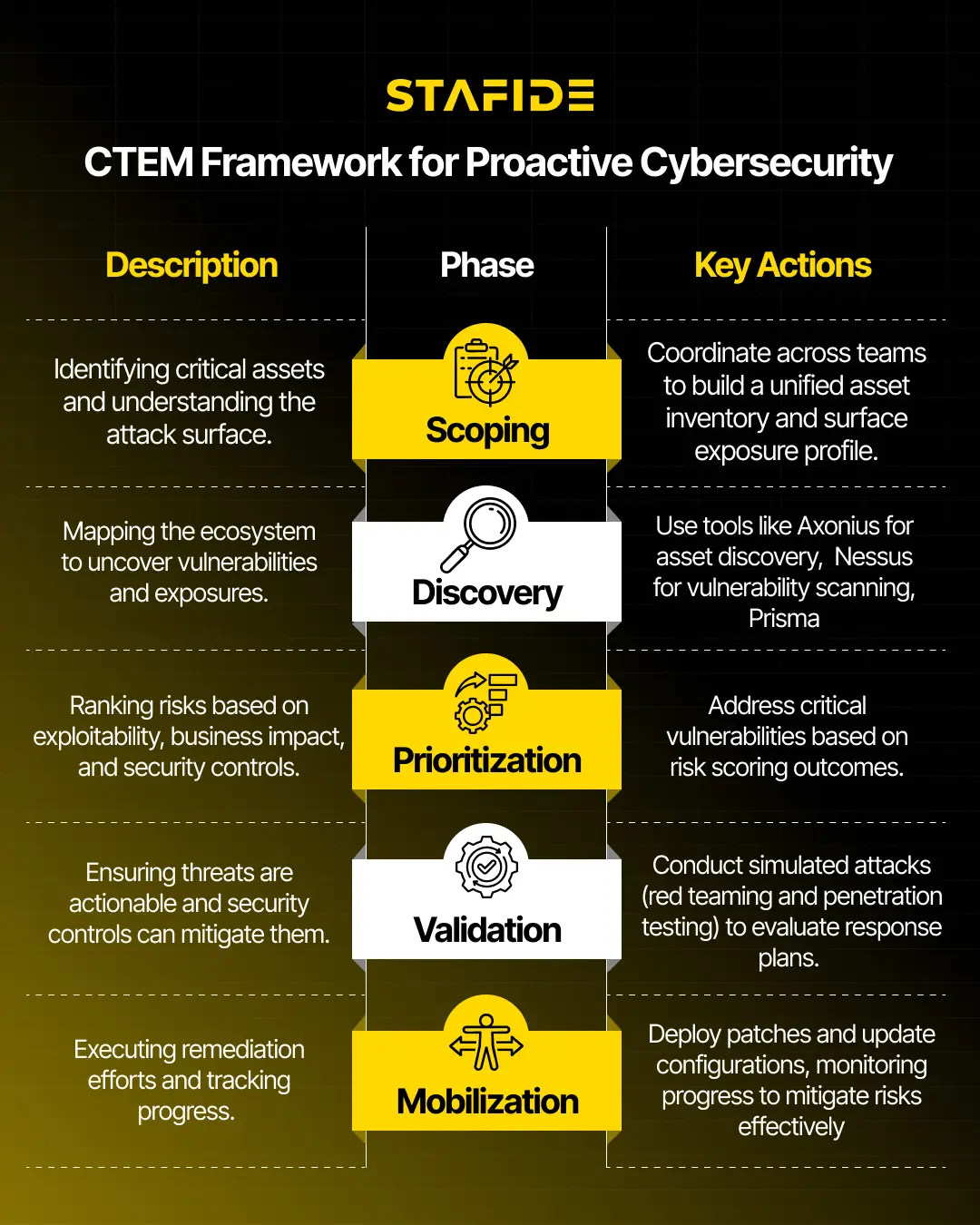
Continuous Threat Exposure Management is designed to provide organizations with real-time visibility into their threat exposure and enable proactive remediation. It operates across five key phases:
- Scoping: Identifying critical assets and understanding the organization’s attack surface. This stage involves input from multiple stakeholders, including IT, Legal, Governance, Risk, and Compliance (GRC), Research & Development, Product, and Business Operations teams.
- Discovery: Mapping out the ecosystem to uncover vulnerabilities and exposures. This phase highlights the importance of robust tooling for discovering assets, misconfigurations, and vulnerabilities. However, substantial human effort is required to classify findings, correlate them with business context, and prioritize them effectively.
- Prioritization: Ranking risks based on factors like exploitability, business impact, and existing security controls. This step ensures that the organization addresses the most critical vulnerabilities first.
- Validation: Ensuring that identified threats are actionable and that security controls can mitigate them effectively. Techniques include simulating attacks through red teaming or penetration testing, testing response plans and mitigation strategies, and verifying the effectiveness of implemented controls.
- Mobilization: Executing remediation efforts and tracking progress. This stage involves coordinating between security and IT teams to address prioritized threats, implementing patches, configuration updates, or new security controls, and monitoring improvements to ensure continuous progress.
The framework’s strength lies in its ability to simulate real-world attacker behavior, measure actual exploitability, and continuously inform remediation strategies. CTEM aligns cybersecurity with business risk in a way that static assessments simply can’t.
But CTEM isn’t just about technology stacks and threat intelligence platforms. It’s a people-powered process that demands multidisciplinary expertise across each phase.
The Human Layer of CTEM
Tools can automate, analyze, and even alert—but they can’t reason, adapt, or collaborate. For CTEM to succeed, it requires skilled professionals who can:
- Translate business risk into technical scope
- Perform deep attack surface analysis
- Contextualize threat data
- Emulate adversarial behavior
- Coordinate and execute remediation efforts
Each of these responsibilities maps to a specific set of roles and skills. Without the right team in place, CTEM becomes a checklist—not a capability.
CTEM Talent Stack: Key Roles That Power Resilience
A successful Continuous Threat Exposure Management (CTEM) program relies on a multidisciplinary team with clearly defined roles:
– CTEM Program Manager: Oversees the entire program, aligning security initiatives with business goals. This role requires strategic vision, technical know-how, and strong leadership to manage cross-functional teams and track KPIs like remediation time and threat resolution effectiveness.
– Threat Intelligence Analyst: Collects and interprets threat data to guide prioritization and response. This role demands strong research and communication skills to turn raw intelligence into actionable insights.
– Vulnerability Management Specialist: Conducts regular scans to identify weaknesses across the IT environment. Expertise in scanning tools, asset inventory, and risk-based prioritization is key.
– Security Operations Analyst: Monitors systems in real time to detect and respond to incidents. Proficiency in SIEM tools and deep knowledge of attack vectors are essential to quickly contain and analyze threats.
– Risk Assessment Specialist: Evaluates the impact of threats and advises on mitigation priorities. Requires fluency in risk frameworks, compliance requirements, and the ability to communicate risks to stakeholders.
– Penetration Tester: Simulates real-world attacks to expose vulnerabilities before adversaries do. This ethical hacker role demands creativity, technical mastery, and continuous learning to stay ahead of evolving threats.
Each role contributes critical expertise to ensure that CTEM efforts are proactive, strategic, and effective across the organization.
The Real-World Challenge: Cybersecurity Talent Shortages
Most organizations today face a daunting reality: the cybersecurity workforce gap continues to grow. According to ISC2’s 2023 Cybersecurity Workforce Study, the global shortage of cybersecurity professionals was estimated at 3.4 million in 2022 and grew to 4 million in 2023. Despite the active workforce reaching an all-time high of 5.5 million, the demand continues to outpace supply. Specialized roles like red teamers or threat modelers are particularly scarce.
ISC2 Cybersecurity Workforce Study
While a skilled, multidisciplinary team is essential for the success of Continuous Threat Exposure Management (CTEM), the growing cybersecurity talent shortage poses a significant challenge. The global cybersecurity workforce gap continues to widen, making it increasingly difficult for organizations to staff the specialized roles CTEM requires. Effective implementation of CTEM is not just about having the right strategy—it’s about having the right people. To move forward, companies must rethink their talent acquisition strategies, invest in upskilling existing teams, and consider partnering with external experts. Without addressing this talent gap, even the most advanced CTEM programs risk falling short of their potential.
People-Powered CTEM: Stafide’s Talent Edge
At Stafide, we specialize in finding the people who can operationalize CTEM at every stage. As cyber threats evolve, organizations must evolve faster. That means moving beyond tools and frameworks and investing in the teams that bring them to life.
Here’s how:
- Expertise in Cybersecurity Talent Acquisition: Stafide helps organizations find skilled professionals proficient in CTEM practices, ensuring that teams are equipped to handle the complexities of modern cybersecurity challenges.
- Tailored Talent Development Solutions: Offering tailored training sessions to upskill existing staff, enabling them to effectively contribute to CTEM initiatives.
- Strategic Consultation: Stafide helps you develop a long-term workforce strategy that evolves with industry demands while integrating CTEM into your processes and aligning security initiatives with your business goals.
CTEM is more than a framework—it’s a capability built by the right people. At Stafide, we find the talent that makes it work.
Ready to close your exposure gap? Get in touch with STAFIDE today.





