Amid the rise of hybrid work, expanding SaaS environments, and constant cyber threats, one fact is clear: you can’t secure what you don’t know. Identity and Access Management (IAM) has evolved from a behind-the-scenes IT function into a critical frontline defense in cybersecurity.
From preventing credential-based attacks to enabling seamless user experiences, IAM has evolved into a strategic pillar for digital enterprises. This blog decodes IAM’s core components, human factors, emerging trends, and best practices—arming CISOs, IT leaders, and security architects with the insights needed to build scalable and secure IAM programs.
Demystifying Identity and Access Management
IAM is the framework of policies and technologies that ensures the right individuals have the right access to the right resources at the right time—for the right reasons.
Why it matters:
- Security: Protects against unauthorized access and insider threats.
- Productivity: Speeds up onboarding/offboarding and reduces IT friction.
- Compliance: Helps meet regulatory mandates (GDPR, HIPAA, PCI DSS).
- Customer Trust: Secure authentication improves user experience and brand confidence.
In a Zero Trust world, IAM is the gatekeeper.
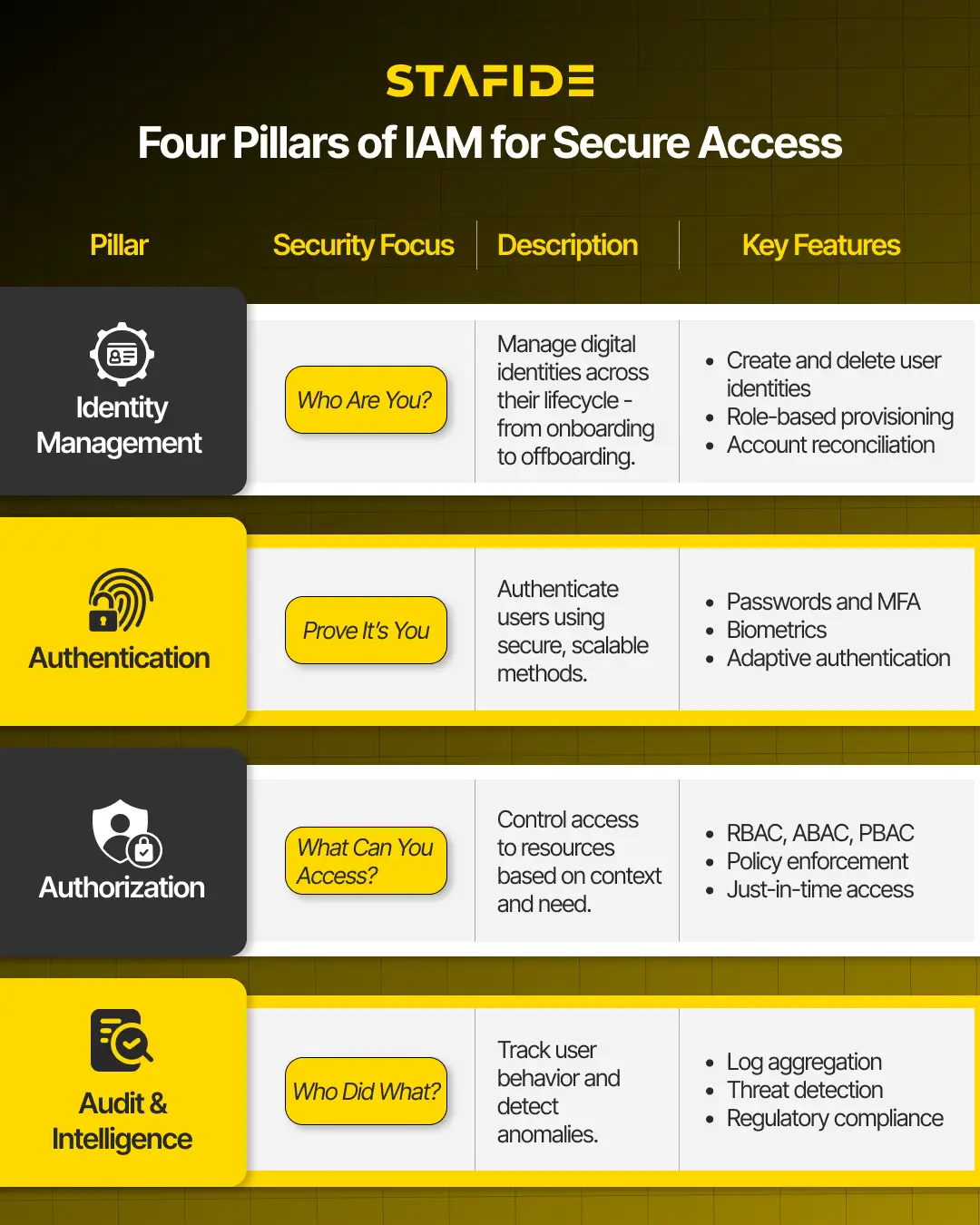
IAM Core Elements
IAM operates across four critical layers:
- Identity Management – Managing digital identities across their lifecycle.
- Authentication – Verifying users via passwords, MFA, biometrics, etc.
- Authorization – Controlling who can access what, and under which conditions.
- Audit & Intelligence – Monitoring and logging for compliance and anomaly detection.
IAM Vendors and Solutions
A variety of vendors offer IAM tools and platforms to help organizations manage identities and access securely and efficiently. These solutions vary in scope—from access management to governance—and are selected based on organizational needs:
- Ping Identity: Offers workforce and customer identity solutions including SSO, MFA, and passwordless authentication.
- Okta: Provides cloud-based identity management with capabilities like SSO, MFA, and lifecycle automation.
- SailPoint: Specializes in identity governance, access certification, and compliance.
- ForgeRock: Delivers unified identity management across workforce, consumer, and IoT environments.
- Microsoft Azure Active Directory: Integrates IAM with Microsoft’s broader cloud ecosystem, supporting Zero Trust strategies.
These platforms are widely implemented across industries to support secure, scalable, and user-centric identity strategies.
IAM Deployment Models
IAM isn’t one-size-fits-all—your choice depends on infrastructure, cloud maturity, and regulations. Each model has unique benefits and trade-offs:
- Centralized IAM: Unified Control
All identity services are managed from a single platform, simplifying governance and compliance. Best for tightly integrated systems but less flexible for multi-cloud or decentralized setups. - Federated IAM: Cross-Domain Access
Uses protocols like SAML, OAuth2, and OpenID Connect for secure access across domains. Supports SSO and BYOI, enhancing user experience but requires strong trust governance. - Cloud IAM (IDaaS): Agile and Scalable
Cloud-native identity via providers like Azure AD or Okta, ideal for cloud-first organizations. Supports MFA and SaaS integration but needs strong vendor oversight and shared responsibility awareness. - Hybrid IAM: Bridging On-Prem and Cloud
Combines on-prem systems like Active Directory with cloud IAM, enabling smooth migration. Adds complexity and requires robust synchronization and monitoring.
Managing Identities Across the Workforce Lifecycle
IAM is dynamic—it evolves with your workforce. As employees, contractors, and partners join, change roles, or exit, their access must be adjusted accordingly to maintain security and compliance.
Lifecycle Management
A strong IAM system supports the full user journey:
- Provisioning: Automatically create accounts and assign roles based on job function.
- Role Changes: Update access as responsibilities shift using RBAC or ABAC models.
- Deprovisioning: Revoke access promptly upon exit to prevent orphaned accounts.
- Reconciliation: Ensure identity consistency across platforms (e.g., AD, SaaS, cloud).
Governance and Control
IAM enforces accountability and regulatory compliance through:
- Policy-based Access: Define who can access what under specific conditions.
- Access Reviews: Regularly audit user privileges to minimize risk.
- Separation of Duties (SoD): Prevent conflicts of interest in critical processes.
- Role Mining: Analyze and streamline access patterns for efficiency and accuracy.
The Power of Automation
Automation reduces errors and improves scalability by:
- Provisioning/deprovisioning accounts
- Enforcing policies in real time
- Flagging anomalies in user behavior
- Automating access approvals and reviews
“IAM automation isn’t just about moving faster—it’s about getting access right every time.”
IAM is most effective when it’s automated, policy-driven, and aligned with every stage of the user lifecycle.
Stronger, Smarter Authentication
The weakest link in security is often a reused password. IAM modernizes this:
- MFA: Adds layers of verification (OTP, biometrics)
- Adaptive Authentication: Adjusts based on device, location, and behavior
- Passwordless: Eliminates passwords with cryptographic keys or biometrics
Result? Reduced fraud and happier users.
Authorization: Access and Control
Effective authorization goes beyond assigning roles—it’s about ensuring users have exactly the access they need, no more and no less. Modern IAM systems implement various models to control access based on organizational complexity and risk tolerance:
- RBAC (Role-Based Access Control): Grants access based on predefined roles, making it easier to manage large groups of users.
- ABAC (Attribute-Based Access Control): Makes decisions using attributes such as department, location, or device type, allowing more dynamic and context-aware access.
- PBAC (Policy-Based Access Control): Uses complex policies that combine roles, attributes, and contextual factors for fine-grained control.
- PAM (Privileged Access Management): Specifically secures high-level accounts by offering just-in-time access, session recording, and credential vaulting to reduce the risk of abuse.
Regardless of the model, the principle of least privilege should guide all access decisions—granting users only the access they need to perform their job.
Zero Trust with IAM
In a Zero Trust security model, nothing is trusted by default—not users, devices, or networks. IAM plays a central role in enforcing this model by ensuring that access is granted only after continuous validation and monitoring:
- Validating identities continuously to ensure users are who they say they are, especially in dynamic or high-risk environments.
- Using contextual signals—like location, device posture, and behavior patterns—to adjust access decisions in real time.
- Logging every access request to maintain an auditable trail for forensics and compliance.
IAM isn’t just a component of Zero Trust—it’s the backbone that makes the model operational, enforcing identity verification at every access point.
The Human Layer: IAM Is a Team Sport
Identity and Access Management isn’t just about technology—it’s fundamentally about people working together across the organization. Success depends on the active participation of multiple stakeholders who each play a vital role in maintaining secure and effective IAM practices:
1. IAM Architects / Strategists
- Design and plan IAM frameworks aligned with business and security goals.
- Deep understanding of IAM technologies, deployment models, and compliance needs.
- Translate complex requirements into scalable IAM solutions.
2. IAM Engineers / Administrators
- Implement, configure, and maintain IAM platforms and tools (Okta, SailPoint, Azure AD, etc.).
- Manage provisioning, authentication methods, access policies, and lifecycle workflows.
- Troubleshoot technical issues and optimize IAM system performance.
3. Access Governance Specialists
- Conduct access reviews, role mining, and policy enforcement.
- Ensure least privilege principles and separation of duties.
- Handle compliance audits and access certification campaigns.
4. Security Analysts
- Monitor identity-related logs and detect anomalies or suspicious behaviors.
- Investigate incidents involving compromised credentials or unauthorized access.
- Support incident response teams with IAM-related investigations.
5. DevSecOps / Developers
- Integrate IAM controls directly into applications and infrastructure pipelines.
- Build authentication and authorization mechanisms in software.
- Automate IAM processes via APIs and scripting.
6. Compliance Officers / Auditors
- Ensure IAM practices comply with regulatory requirements (GDPR, HIPAA, PCI DSS).
- Perform regular audits and risk assessments focused on identity access.
- Maintain audit trails and documentation for governance.
7. User Support and Training Specialists
- Educate end users on security best practices (MFA usage, phishing awareness).
- Support password resets, account recovery, and access requests.
- Drive adoption and user satisfaction with IAM tools
Because IAM impacts all these groups, collaboration and clear communication are non-negotiable. Only through coordinated effort can organizations build a strong, resilient IAM program that effectively balances security and usability.
IAM in the Cloud Era
The rise of cloud and hybrid environments has introduced new complexities to Identity and Access Management. Managing identities across diverse platforms—ranging from on-premises systems to multiple cloud services—requires a flexible and unified approach. Cloud-native IAM solutions like AWS IAM and Azure Active Directory provide foundational identity services tailored for cloud infrastructure, but organizations often face the challenge of integrating these with their existing legacy systems. Ensuring consistent access policies across Software-as-a-Service (SaaS), Infrastructure-as-a-Service (IaaS), and Platform-as-a-Service (PaaS) environments is critical to maintaining security and compliance.
To address these challenges, modern IAM platforms must be:
- API-first, enabling seamless integration with various applications, cloud services, and security tools.
- Extensible, so they can adapt to evolving business needs and incorporate new identity sources or access models.
- Resilient, capable of maintaining secure and reliable identity services across distributed and hybrid infrastructures.
By embracing these principles, organizations can achieve centralized control, better visibility, and stronger security across their increasingly complex IT ecosystems.
Mastering IAM Challenges
Tackling Credential Theft and Orphaned Accounts
Credential theft remains a major risk but can be reduced with multi-factor authentication (MFA) and passwordless methods, adding layers beyond passwords. Orphaned accounts—active after employee departures—pose hidden threats; automated deprovisioning promptly disables these accounts to close gaps.
Managing Overprivileged Users
Users with excess access increase risks of misuse. Applying least privilege and regular access reviews ensure permissions stay appropriate and aligned with business needs.
Addressing Shadow IT and Building a Secure Culture
Shadow IT bypasses controls and risks data leaks. Combating it requires improved visibility, consistent policy enforcement, and combining automation with strong governance and security awareness culture.
What’s Next: IAM Trends to Watch
- Decentralized Identity: Blockchain-based user-owned credentials
- AI/ML: Behavior-based access decisions
- Continuous Access Evaluation Protocol (CAEP): Real-time access adjustments
- IDaaS Expansion: IAM as a Service becomes the norm
Stay proactive to stay protected.
Best Practices for Modern IAM
- Enforce MFA across all user groups
- Eliminate standing privileges with PAM
- Automate lifecycle and certification workflows
- Integrate IAM with SIEM and SOAR tools
- Build IAM into your DevSecOps pipeline
- Conduct regular audits and red teaming
IAM isn’t a set-and-forget—it’s a living framework.
Conclusion: People Power IAM Success
While cutting-edge tools and automation are essential to modern IAM, the true strength lies in the people behind it. From vigilant end users to diligent managers, skilled security teams, and proactive compliance officers, effective identity and access management is a team effort. Technology provides the framework, but human collaboration, awareness, and accountability are what transform IAM from a technical function into a resilient security foundation. Investing in talent, training, and cross-team communication is just as critical as deploying the latest platforms—because in IAM, people are the ultimate gatekeepers of trust and security.
Need expert support to build your IAM team?
Stafide helps you find the right human expertise to support and enhance your IAM initiatives, ensuring the people behind the technology drive lasting security and success.
Connect with us to learn how we can assist in building the IAM team your organization needs.